How Sycope helps:
· Real-time traffic flow monitoring shows top talkers and bandwidth hogs
· Detects spikes in volume across interfaces, segments, or applications
· Dynamic baselines help distinguish between normal peaks and anomalies
How Sycope helps:
· Visualizes traffic distribution across multiple paths or links
· Detects asymmetric routing and uneven traffic loads
· Identifies underutilized vs. overloaded interfaces
How Sycope helps:
· Measures application response time (L7), TCP round-trip time, and retransmissions
· Identifies where in the chain (user ↔ app ↔ DB) the delay occurs
· Detects slow handshake patterns and degraded sessions
How Sycope helps:
· Identifies inefficient WAN usage (e.g., backup running during peak hours)
· Analyzes flows between sites and clouds for bottlenecks
· Helps prioritize traffic with policy validation and visibility
How Sycope helps:
· Detects outdated or unsupported protocols (e.g., Telnet, SMBv1)
· Identifies misbehaving or unauthorized applications
· Uses L7 app recognition and customizable detection rules
How Sycope helps:
· Analyzes DSCP tags and queue utilization (if exposed by flow data)
· Identifies dropped or delayed packets linked to QoS violations
· Highlights traffic types most affected by congestion
Sycope helps by:
· Detecting threats based on MITRE ATT&CK techniques
· Identifying early signs of ransomware, C2 communication, and lateral movement
· Enabling proactive incident response with built-in detection rules
Sycope helps by:
· Matching actual traffic against expected behavior via Traffic Rule Profiles
· Detecting policy violations in real-time
· Enabling forensic validation for audits and incident reviews
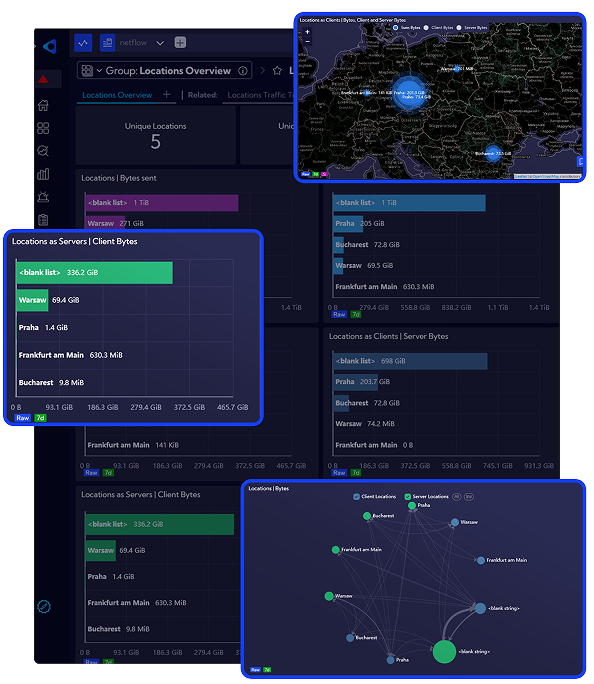
Full insight into the operation of the IT network, allowing to make quick decisions about resource allocation and actions to protect against unplanned downtime.
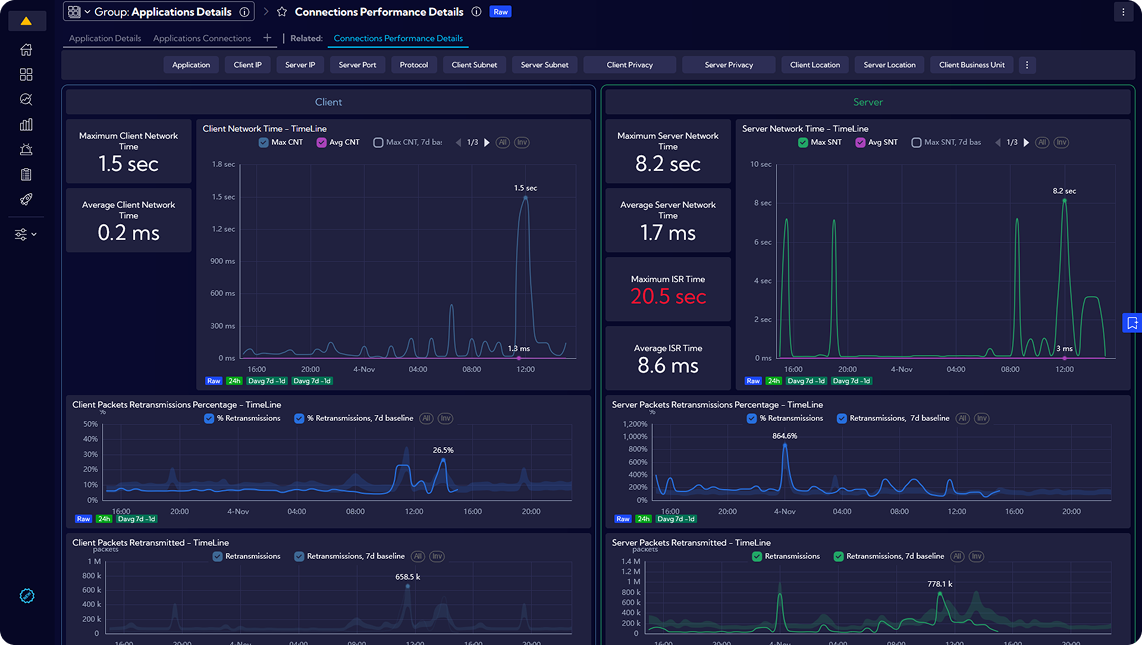
Critical performance metrics measurements in any infrastructure. Focused on L4-L7 monitoring, from TCP analytics to L7 app detection and apps response times measurements.
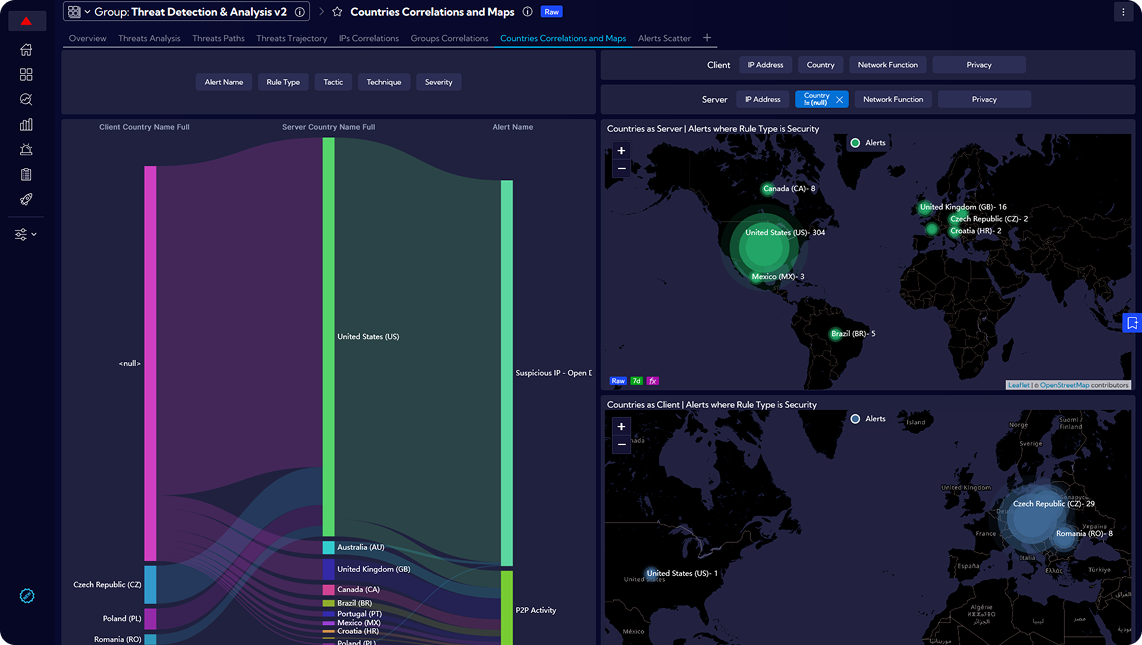
Sycope detects and analyzes security anomalies and threats across the entire organization using the MITRE ATT&CK framework. This helps identify real attacks faster and reduce the risk of breaches.
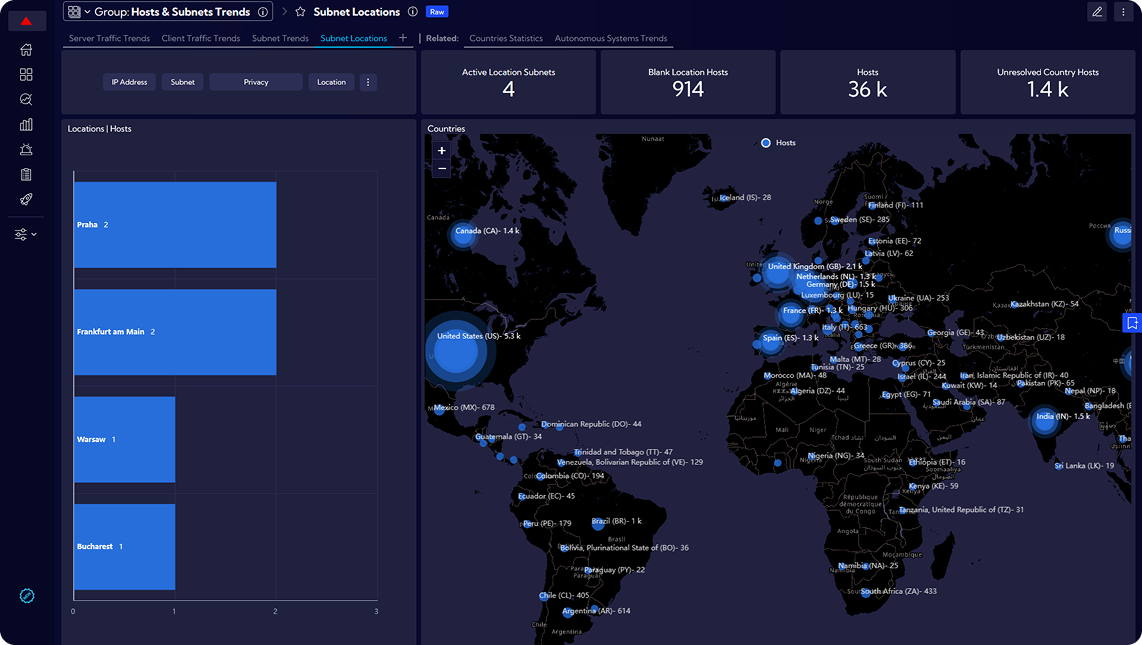
Real-time, automatic inventory tracking, monitoring devices and their associated assets using NetFlow data and dependency mapping.